IndexFiguresTables |
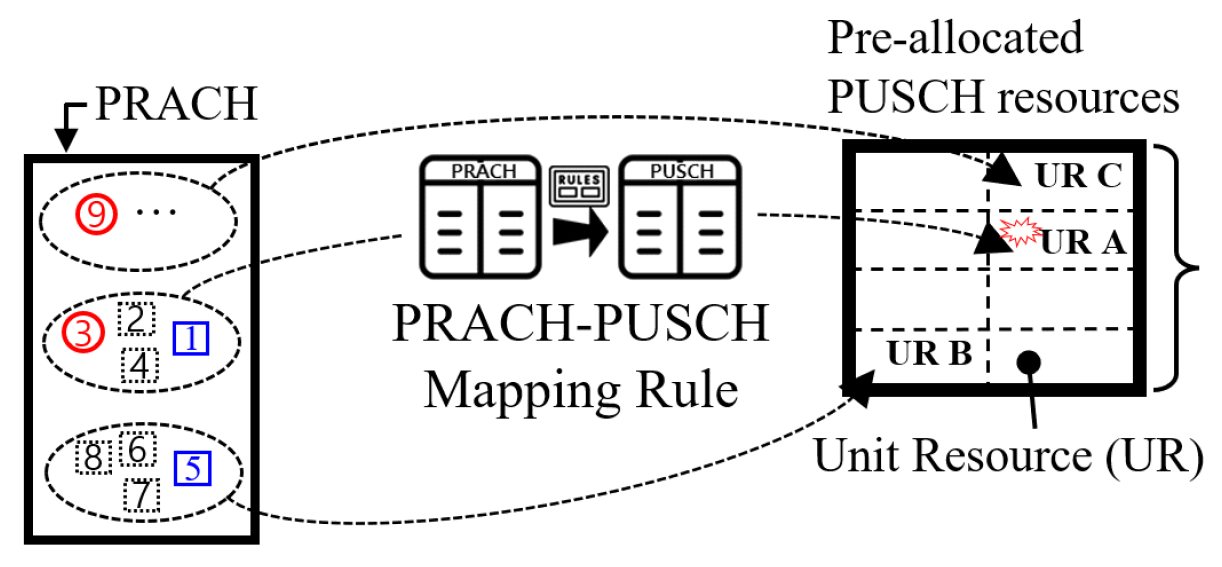
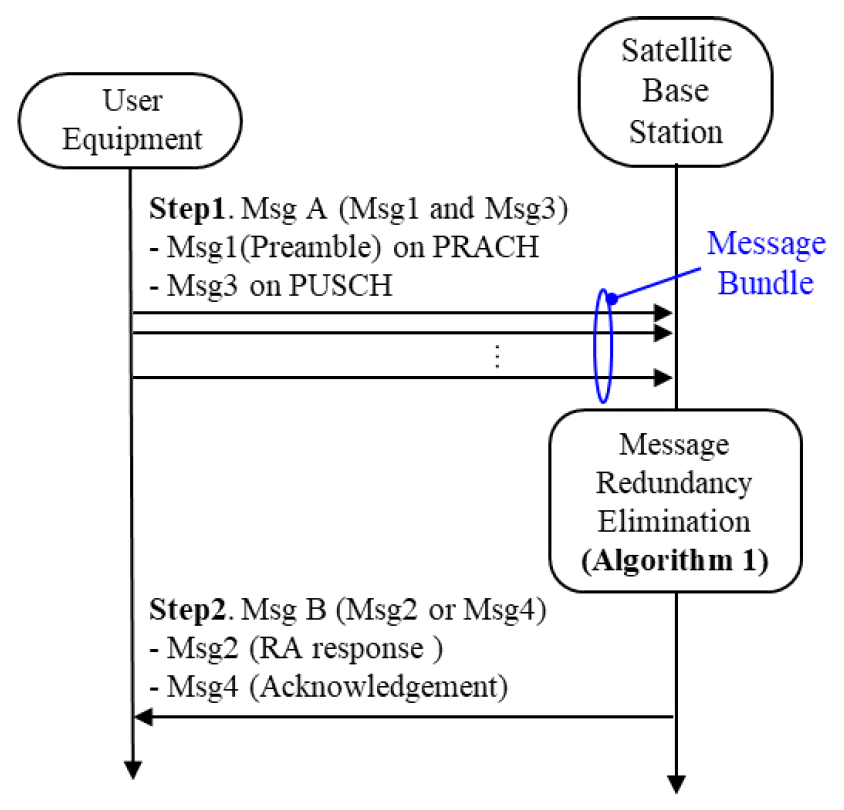
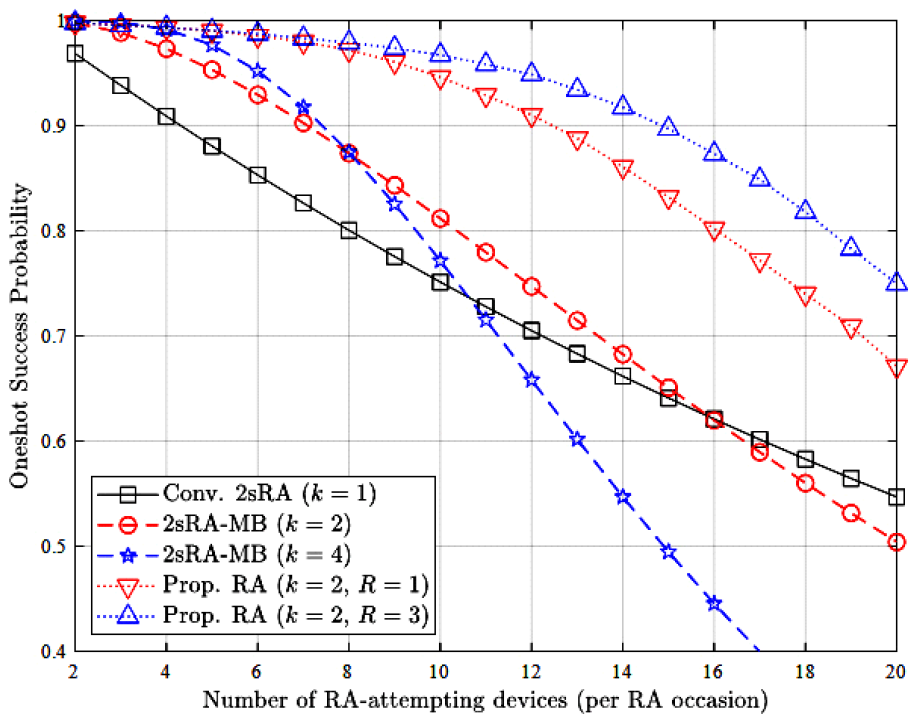
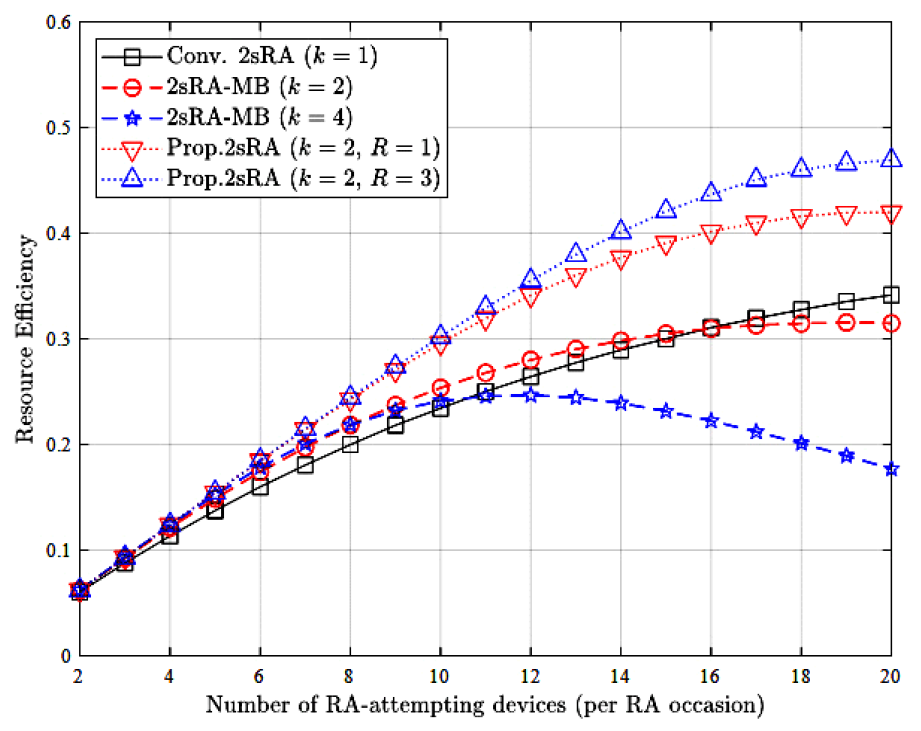
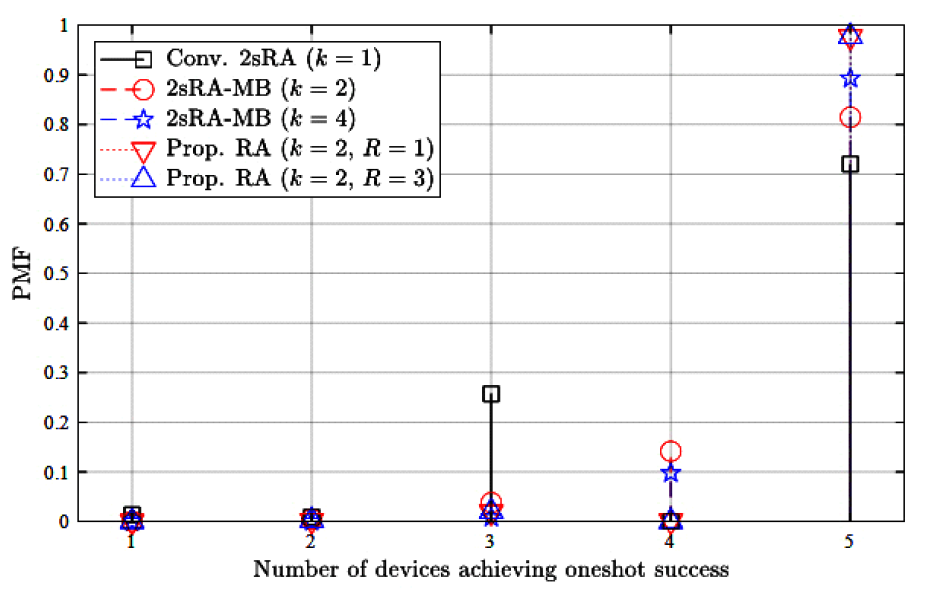
Taehoon Kim , Seong Ho Chae and Inkyu BangA Redundancy-Aware Two-Step Random Access for LEO SatelliteAbstract: In this letter, we propose a redundancy-aware two-step random access (2sRA) for LEO satellite networks. We investigate key features of message bundling (MB), and message redundancy elimination (MRE) techniques and integrate them into the 2sRA framework. In our proposed scheme, each user equipment (UE) can initiate multiple RA attempts in parallel using the MB technique, while the base sta- tion (BS) retains the collided payloads and attempts to recover them using successfully decoded payloads, leveraging the MRE technique. Simulation results demonstrate that our proposed scheme significantly improves both access success probability and re- source efficiency. Keywords: LEO Satellite Networks , Two-Step Random Access , Message Bundling , Redundancy Elimination 1. IntroductionLow earth orbit (LEO)-based non-terrestrial networks are emerging as a key infrastructure component of 6G mobile communication systems[1]. Although LEO satellite networks operate at lower altitudes compared to medium earth orbit and geostationary orbit satellites, they still experience higher propagation delays than terrestrial networks. To access internet services via satellite networks, each UE must establish a connection with a satellite BS through a random access (RA) procedure[2]. To facilitate rapid network access, a number of studies have aimed to alleviate the collision problem inherent in the conventional four-step RA (4sRA) procedure[ 2,3]. However, due to the long propagation delays between ground stations and LEO satellites, signaling overhead must be minimized to achieve the low-latency requirements of satellite communications. Accordingly, several recent studies have explored simplified two-step random access (2sRA) procedures, as specified in 3GPP Release 16[4-6]. Kim et al.[7] proposed a novel 2sRA scheme with message bundling (2sRA-MB) technique to enhance the network access performance, where a key feature is the support for simultaneous multiple RA attempts. However, as the number of RA participants increases, the performance degrades and can become even worse than that of the conventional 2sRA scheme. To address this issue, we propose a redundancy- aware 2sRA scheme that integrates two message redundancy management techniques: MB and message redundancy elimination (MRE). Simulation results verify that our proposed scheme offers substantial improvements in both access success probability and resource efficiency. Ⅱ. Redundancy-Aware Two-Step Random AccessThis section presents background information on the 2sRA framework, along with key features of the MB and MRE techniques. Subsequently, we describe the overall procedure of our proposed scheme. 2.1 Background and Key FeatureThe 2sRA simplifies the conventional 4sRA procedure into two signaling steps, where the preamble (Msg1) and the payload (Msg3) are transmitted simultaneously. To enable this, the BS pre-allocates a portion of the physical uplink shared channel (PUSCH) resources, which are composed of multiple unit resources (URs). Here, we denote the amount of pre-allocated PUSCH resources as Ω. Fig. 1 illustrates an example of the mapping relationship between preambles (PAs) and URs, where multiple PAs are pre-associated with a single UR. In this example, each group of 4 PAs are mapped to each UR, and a total of 8 URs are configured within the pre-allocated resources (i.e., Ω=8). When the MB technique is applied[7], identical messages can be simultaneously transmitted over multiple URs associated with randomly selected multiple preambles. Fig. 1 depicts a scenario in which UE 1 selects both PA 1 and PA 5, while UE 2 selects PA 3 and PA 9. According to the predefined PAs–URs mapping rule in this example, UE 1 transmits its payloads over UR A and UR B, whereas UE 2 transmits its payloads over UR A and UR C. Note that PA 1 and PA 3 are grouped together and mapped to UR A, resulting in a payload collision. However, since additional identical messages are transmitted via different URs, both UEs can successfully complete their RA attempts. We further focus on UR A, where the collision occurs. If the BS successfully decodes a payload transmitted via UR B (or UR C), it can subtract the corresponding signal component from the received signal on UR A. This interference cancellation enables an additional opportunity to decode the residual signal in UR A. We refer to this approach as the MRE technique. The MRE technique is expected to enhance network access performance, particularly by improving the one-shot success probability, which facilitates more radio-efficient operation within the 2sRA framework. 2.2 ProcedureFig. 2 shows the overall procedure of our proposed scheme. 1) Step 1. Multiple Transmissions of MsgAs using Message Bundling Each UE prepares k replicas of the original payload (i.e., Msg3), where k represents the number of selected PAs associated with distinct URs. Thereafter, it randomly select k PAs and transmits each of k payloads on each of URs associated with the selected PAs. 2) Step 2. Message Redundancy Elimination and Transmission of MsgB The BS attempts to decode payloads according to Algorithm 1. In particular, it iteratively performs MRE using the successfully decoded messages until no additional messages can be recovered or the number of iterations reaches R , which denotes the maximum number of iterations allowed for the elimination procedure. If a payload is successfully decoded, the BS transmits Msg B containing an acknowledgment (ACK). Otherwise, Msg B includes a random access response (RAR), prompting the recipient to fall back to the conventional 4-step RA (4sRA). Ⅲ. Numerical Results & DiscussionsWe perform simulations with MATLAB to evaluate the performance of our proposed scheme. Message bundling is basically assumed[7] (i.e., k = {2, 4}), and we here focus on evaluating the effect of the MRE technique on [TeX:] $$p_s \text { and } \eta$$ for varying n, where n is the number of RA-attempting UEs per RA occasion (RAO). Here we consider two primary performance metrics [TeX:] $$p_s \text { and } \eta$$. Let [TeX:] $$p_s$$ denote the probability of successful access without fallback to the 4sRA (referred to as one-shot success probability), which is given by [TeX:] $$p_s=\frac{n_s+n_r}{n} \text {, where } n_s \text { and } n_r$$ represent the number of UEs successfully completed RA attempt without fallback and the number of additional successful UEs due to the redundancy elimination process.1) Furthermore, let η denote the resource efficiency defined as the ratio of the number of RA-successful UEs to the amount of pre-allocated resources, Ω, which can be further expressed as [TeX:] $$\eta=\frac{n_s+n_r}{\Omega} .$$ 1) [TeX:] $$p_s \geq 1-\sum_{m=0}^k(-1)^m\left(\frac{\left(\frac{M}{G}-k\right)!\left(\frac{M}{G}-m\right)!}{\left(\frac{M}{G}-m-k\right)!\left(\frac{M}{G}\right)!}\right)^{n-1}\binom{k}{m}[7] \text {. }$$ Fig. 3 shows [TeX:] $$p_s$$ for varying n. With our proposed scheme, [TeX:] $$p_s$$ can be significantly improved even in a relatively large n regime, compared to the benchmark schemes: the conventional 2sRA[4] and the 2sRA-MB[7]. Furthermore, the higher [TeX:] $$p_s$$ can be achieved if the larger R is applied. It is worth noting that integrating the MRE technique into the 2sRA-MB scheme (i.e., our proposed scheme) yields better performance than simply increasing the value of k in the 2sRA-MB. Furthermore, even with a small value of R significant performance gains can be achieved compared to the baseline schemes. Therefore, the value of R should be carefully selected, taking into account the computational complexity of Algorithm 1. Fig. 4 shows η for varying n. From the results, we can verify that our proposed scheme can achieve better η compared to the benchmark schemes, and η increases as R increases. Fig. 5 shows the distribution of the number of UEs achieving one-shot success without falling back to the 4sRA when 5 UEs attempt 2sRA at the same time. Compared to the baseline schemes, we verify that our proposed scheme can provide quick access capability to more UEs. References
|
StatisticsCite this articleIEEE StyleT. Kim, S. H. Chae, I. Bang, "A Redundancy-Aware Two-Step Random Access for LEO Satellite Networks," The Journal of Korean Institute of Communications and Information Sciences, vol. 50, no. 10, pp. 1564-1567, 2025. DOI: 10.7840/kics.2025.50.10.1564.
ACM Style Taehoon Kim, Seong Ho Chae, and Inkyu Bang. 2025. A Redundancy-Aware Two-Step Random Access for LEO Satellite Networks. The Journal of Korean Institute of Communications and Information Sciences, 50, 10, (2025), 1564-1567. DOI: 10.7840/kics.2025.50.10.1564.
KICS Style Taehoon Kim, Seong Ho Chae, Inkyu Bang, "A Redundancy-Aware Two-Step Random Access for LEO Satellite Networks," The Journal of Korean Institute of Communications and Information Sciences, vol. 50, no. 10, pp. 1564-1567, 10. 2025. (https://doi.org/10.7840/kics.2025.50.10.1564)
|